We live in a world where everyone uses the Internet, security and privacy is crucial. Online privacy refers to the protection of personal information and data. In cybersecurity, you protect sensitive data from unauthorized access, control information shared online, and determine which data is shared with third parties. VPNs can be used for many things today, like watching blocked content, trading anonymously, streaming, and gaming. When using a VPN, the question arises: are VPNs safe? Yes, this is the answer. Users can use VPNs when using public networks to establish a protected connection. You can hide your online identity and encrypt your internet traffic with VPNs. This way, third parties can’t track your online activities and steal your data. Real-time encryption. In the following, we will talk more about the evaluation of VPN security and describe methods so that you can determine Is VPN safe.
Understanding VPN Encryption
In order to know that are vpns safe, you need to know the type of encryption. Security and privacy are important.
Encryption protocols used by VPNs
Understanding the types of encryption protocols can help you answer the question of are vpns safe more easily. Different VPNs use different protocols, which makes them unique. Depending on the protocol, your data may be encrypted with more or less bandwidth. They may be outdated or too new to offer complete protection. Choosing the proper VPN protocol and understanding how it works is crucial to your overall online security, and is vpn safer.
OpenVPN
The OpenVPN protocol is widely used in VPNs. The solution is highly secure and open-source. Different encryption protocols can customize the security level of OpenVPN based on the user’s needs. With all its versatility, setting up OpenVPN can be challenging.
WireGuard
The effectiveness of WireGuard is still being investigated, and it is still a reasonably new VPN protocol. With WireGuard, you can browse the web more quickly than with other VPN protocols. This protocol looks promising but lacks key features, such as complete anonymity for users.
L2TP/IPsec
Layer 2 tunneling protocol, as its name suggests, is a tunneling protocol for VPNs. In tunneling, data is transported using protocols not supported by the network. By placing packets of information inside another supported packet, tunneling moves information. Unfortunately, encryption and authentication are not included. You are only connected to your VPN server through it. IPSEC is used to encrypt L2TP traffic. Data is encrypted using different protocols in IPSec. Many systems support L2TP, which is highly adaptable in terms of security. While it is fast, it may be compromised by the National Security Agency and has trouble getting through firewalls.
IKEv2
A reliable VPN protocol is Internet Key Exchange version 2, or IKEv2. The protocol provides secure encryption. Regardless of where you connect to the internet, it uses minimal bandwidth. IKEv2’s only downside is its limited compatibility.
SSTP
Because Microsoft owns SSTP, Windows OS supports it. To ensure its security, it also uses AES-256 encryption. Concerns have also been raised regarding Microsoft’s collaboration with the NSA.
PPTP
One of the first VPN protocols was the Point-to-Point Tunneling Protocol. Security concerns include weak encryption protocols and decryption by the NSA, which is frequently blocked by firewalls. The speed and compatibility of this program are excellent, but its security concerns outweigh its advantages. Overall, PPTP is not a secure VPN solution.
The role of encryption in ensuring VPN security

You can protect yourself from the following cyber threats with a VPN , and Understanding are vpns safe, you should know Encryption, and attacks related to it:
Man-in-the-middle attacks
Cybercriminals intercept data sent between businesses or individuals through man-in-the-middle attacks. The purpose of intercepting data can vary, but cybercriminals often look to eavesdrop, steal, or modify it. Typically, MITM attacks occur on public WiFi networks since anyone can connect to them and see the data sent over them.
Through encryption, VPNs protect your internet traffic from being intercepted, so anyone can’t see what’s sent or received by your device. Next time, connect to a VPN before connecting to a public WiFi network to keep your information secure.
Remote hacking
A remote hack is when cybercriminals gain unauthorized access to a device or network remotely. Using your IP address is one of the most common ways cybercriminals carry out remote hacking attacks. It is difficult for cybercriminals to know your IP address when you use a VPN. By doing so, they cannot hack your network or device remotely.
DDoS attacks
Distributed Denial-of-Service (DDoS) attacks disrupt your server by flooding it with an overwhelming amount of internet traffic. Users of the targeted website become unable to access the website due to DDoS attacks overloading servers with traffic. DDoS attacks require cybercriminals to know your IP address. By masking your IP address, VPNs prevent cybercriminals from targeting your network for DDoS attacks.
Session hijacking
Have you ever noticed that you don’t have to consistently reenter your credentials when logging in to one of your accounts? You are creating a session ID when you log in to your account on the website. Cybercriminals often exploit session IDs to compromise your accounts, even though they provide convenience. A session hijacking attack occurs when cybercriminals use your session ID to trick the website server into thinking they are you.
You can encrypt all your internet activity using VPNs, including your session ID. It is challenging for cybercriminals to steal your session ID and use it to compromise your account.
Advantages of Using Encryption
VPNs and encryption can protect your online privacy in several ways.. This topic also helps you to know is a vpn safe. Here are a few::
- Security:Encryption and VPNs add an extra layer of protection when browsing the web, making sensitive data less susceptible to interception;
- Anonymity: VPNs mask the user’s IP address to prevent tracking of their online activities.;
- Geo-restricted Content: Users can access geo-restricted content through VPNs, including streaming services and websites that are not available in their country;
- Public Wi-Fi protection: Virtual private networks (VPNs) and encryption can protect users using public Wi-Fi networks;
VPNs and Encryption: Limitations and Risks
There are some limitations and potential risks to consider when using encryption and VPN for online privacy. Some of these include:
- Reduced Speed: VPN servers can cause data encryption to slow down internet speeds, which may be an issue for some users;
- Adaptability : Depending on the device and software, some encryption and VPN protocols may not work correctly, which could limit their effectiveness;
- Invalid sense of security: Although encryption and VPNs can provide significant protection, they are not foolproof. They should not be relied upon as the sole means of protecting online privacy. Strong passwords and avoiding suspicious links and downloads are still good online hygiene practices.
- VPN Providers’ Trustworthiness: It is essential for users to carefully research and choose a VPN provider that offers the level of security and privacy they claim. Furthermore, some VPN providers may keep logs of users’ internet activity, which third parties can access.
Consider these things when evaluating VPN security and answering are vpns safe
VPN Provider Trustworthiness

No-log policies and data retention practices
VPNs with poor logging policies are very risky to use. Among these risks is the breach of trust. When you use a VPN, you trust the provider with your data and expect them to keep it secure. When you use a VPN, you trust the provider with your data and expect them to keep it secure. A provider who maintains extensive logs and misuses data blatantly violates trust.
Legal requests for user data are directly affected by logging policies. VPN providers can become legally obligated when a criminal investigation or court order comes along. As a result, if the data is stored, it may have to give over user information, like browsing history. This means the no-logs policy can offer the best protection for online privacy, even if the provider hasn’t stored anything.
Evaluation of VPN providers’ claims
Several aspects of a VPN’s logging policy should be considered when evaluating it:
- A no-log policy: An ideal VPN logging policy is a no-log or zero-log policy. Providers follow this policy to ensure they don’t store any data passing through their servers. The data remains safe even if the provider is subpoenaed or hacked since there is no data to give or steal. When choosing a VPN, you should aim for this level of privacy;
- Having transparency: Another factor worth mentioning is transparency. VPN providers who are transparent about logging policies are trustworthy. You must clearly explain what information is being collected, why it is being collected, and how long it will be stored. Also, they must clearly outline how they will deal with legal requests for data. Before choosing a VPN, thoroughly read its privacy policies and terms of service.
- Policy on data retention: Data retention refers to how long a VPN provider keeps your data. Even if a VPN provider collects some data, it doesn’t have to be a deal-breaker if they don’t store it for a long time. In general, the shorter the data retention period, the better it is for your privacy. After your session ends, you should look for providers that delete your data within a few hours or, at most, a few days;
Jurisdiction and legal obligations
The law must be followed in accordance with local regulations. Some countries require data logging, and some have strict anti-logging policies. Various regulations exist in different countries, making compliance challenging for international businesses.
Impact of local laws on VPN security
- VPN Privacy Rights: The right to privacy of internet users is subject to local laws governing internet usage and surveillance. Also, Using a VPN can be a red flag for authorities in some countries;
- VPN Guidelines for Responsible and Legal Use: In their country, VPN users should be aware of the legal implications. The use of VPNs for illegal purposes can lead to legal consequences;
Potential Security Risks and Vulnerabilities
VPN Leaks
Your IP address can be leaked in several ways:
- DNS leaks: When you type a URL, your web browser requests a DNS server to resolve a domain name into an IP address. Your IP address can be exposed if your web browser leaks your DNS requests;
- WebRTC leaks: WebRTC allows real-time communication between web browsers. You can use it for video conferencing, voice calling, and file sharing. WebRTC can also leak your IP address, even if you are using a VPN or proxy server;
- IPv6 leak: Currently, most websites only support IPv4, but quite a few internet service providers (ISPs) support IPv4 and IPv6. Your ISP uses both protocols, but you connect to a website or service that only supports IPv4. It is here that IPv6 leaks may occur – the requests you send to a website or service will contain both IPv4 and IPv6 addresses;
Ways to detect and prevent IP leaks
- Consider using HTTPS: Using HTTPS on your website will prevent man-in-the-middle attacks and encrypt your users’ data during transmission.
- Consider using a VPN service: Make sure your users use a Best VPN Such as esthervpn that doesn’t leak IP addresses;
- Be sure to implement DNS leak protection: By implementing DNS leak protection, you can ensure your DNS requests are not leaked;
- Turn off WebRTC: Your website should disable WebRTC by default to prevent IP addresses from being leaked;
- Install an ad-blocker and anti-tracking extension: Anti-tracking extensions and ad-blockers can help prevent websites from tracking your online activity;
- Make use of antidetect browsers: By using proxies, VPNs, and other privacy-enhancing tools, antidetect browsers can prevent IP leaks. Antidetect browsers may even include features like automatic IP rotation and user agent switching, which can help prevent IP leaks and make it harder for websites to track you;
Insecure VPN Protocols and Outdated Encryption
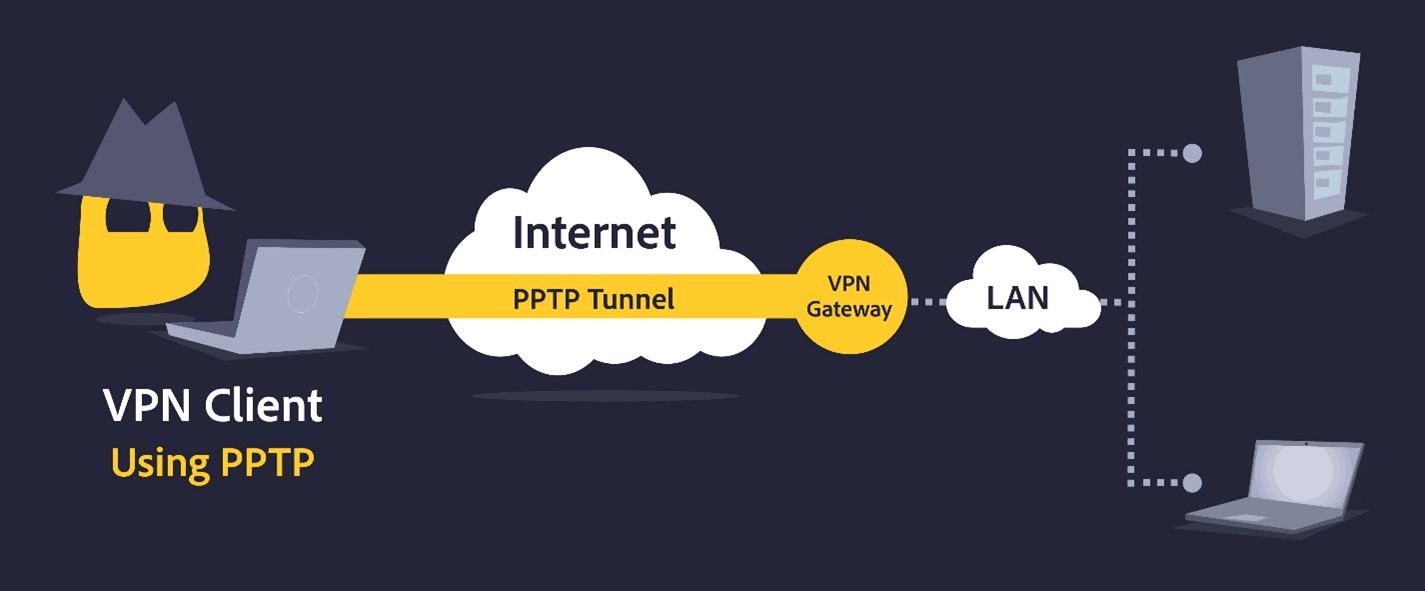
Risks associated with older protocols like PPTP and L2TP/IPSec
- It’s slow: L2TP is slower than other VPN protocols;
- Controversy surrounding the NSA: L2TP VPN is potentially compromised when combined with IPSec encryption, as the NSA has allegedly cracked it;
- Problems with firewalls: L2TP VPNs struggle to bypass firewalls, preventing users from unblocking websites or accessing specific systems;
- Insecure: PPTP is not as secure as modern VPN protocols. If a person has the right tools, the protocol’s encryption can be cracked, exposing your data;
Importance of using secure and up-to-date protocols
The majority of VPN protocols either handle data encryption and authentication or connection speed, but rarely both at the same time. Newer VPN protocols like WireGuard aim to offer both to users. Use OpenVPN, and IKEv2/IPSec if security is more important to you or your organization.
Malicious VPN Apps and Services
Risks of using free or unknown VPN providers
- A limited number of features: Most free VPNs offer limited features that may not meet your privacy and security needs. It is often difficult to find advanced features like split tunneling, which splits your internet traffic and sends some of it through your VPN and the rest through an open network, and the ability to bypass geo-restrictions for streaming if you prefer to bypass other countries’ geo-restrictions. These limitations can significantly affect your online experience and may not provide the protection you want;
- Security flaws: A VPN provides robust encryption protocols that secure your data, which is one of the primary reasons to use one. Unfortunately, many free VPNs still use weak encryption protocols like PPTP, exposing you to hacker attacks and data theft;
- Caps on data: Free VPN services typically restrict the amount of data that can be transferred. For example, watching high-quality videos or streaming games can be particularly problematic if you are a heavy user. When you reach your data cap, you won’t be able to use the VPN until the data cycle starts over, which is usually every month.
- A slow speed: If a VPN is free, users will flock to it. It can result in overcrowded servers, which slow down connection speeds, cause high latency, and cause buffering. Streaming, gaming, and browsing will all be affected. VPNs slow your speeds somewhat, but the slowdown won’t be noticeable if you use a fast VPN;
- Server options are limited: Having fewer servers to choose from is a minor deal. Still, a free VPN can make providing a reliable and fast connection challenging. Geo-restricted content is also harder to access;
- Viruses: Unknown and less reputable free VPNs could have malware hidden in their software, putting your device and personal information at risk. By downloading a potentially malicious VPN, you put yourself at risk of hacking and data theft;
- Data collection: Many free VPNs collect and sell your browsing data to third parties, which defeats the purpose of using a VPN to protect your privacy. The free VPN can result in targeted ads, privacy breaches, and even identity theft if data is collected like this;
- Ads and pop-ups: Free VPNs rely on advertisements to make money. Because of this, you may be bombarded with intrusive ads and pop-ups while using the service;
Best Practices for Secure VPN Usage
Choosing a Reputable VPN Provider
Factors to consider
These factors will help you make a better decision, are vpns safe:
- No-logs policy: A strict no-logs policy prohibits the recording of your online activities;
- encryption standards: Look for a VPN with strong encryption to ensure your data remains secure during transmission;
- Jurisdiction: Find out where the VPN server is located. Data retention laws and privacy regulations vary from state to state;
Among the different VPNs, Esthervpn is the most reliable VPN. Because it is highly secure and does not have any security flaws. So don’t miss the opportunity and download Esther VPN right now.
Enabling Additional Security Features
Knowledge of additional features is also important in evaluating VPN security and answering the question are VPNs safe:
Split Tunneling
Split tunneling separates your internet traffic in a VPN. Some of it travels through a secure VPN tunnel, while the rest goes directly to the internet. You can use the VPN for remote network access, such as corporate email and files while browsing the web or streaming media via your regular internet connection.
Kill Switch
Whenever a VPN connection drops, a VPN kill switch disconnects the device from the internet, preventing data from being transmitted unencrypted.
Kill switches work by continuously monitoring the VPN connection. If they detect a drop, they immediately block all internet traffic until the VPN connection is restored. This feature keeps online activities private and secure when using public or untrusted networks.
Double VPN configurations
Multi-hop VPNs are advanced security features that encrypt your data twice and provide greater anonymity by routing online traffic through two VPN servers. Double VPNs encrypt data from your device and route it via a remote VPN server. The data is then re-encrypted by a second VPN server. Your online activity is hidden behind two servers by chaining two VPN servers, doubling its security.
Verifying VPN Functionality and Security
You can use the following tools to evaluate VPN security and DNS/IP leak tests:
- VPN Leak Test Websites;
- org;
Conclusion
When using the Internet and VPN, you may face various security risks such as DNS/IP leak, WebRTC, and Man-in-the-Middle attacks. It’s even possible that your data could be targeted by the government. This underscores the need to be vigilant about your security when online. However, by using a secure VPN, you can connect to the Internet with a high level of security and without any issues. Esthervpn is a service that can provide this peace of mind. So, take the step to download VPN now and ensure your online security.